How to hack windows 2000 using nessus.....
What is
nessus?
Nessus is a propriety vulnerability scanner developed
by tenable network. It is free of charge for personal use in a non-enterprise
environment.
We use kali Os to hacking
windows server, to testing vulnerabilities .
- · In Linux we have to search both Os are in the same network. And search the ip address of each systems.
- · To Linux : Open terminal and type “ifconfig”

- · Ten now we have both ip addresses. Using ping command can check the connection between each other.
Ex: ping 192.168.55.99
- · Then both are connected we can start the nessus and can find the vulnerabilities.
· Using “service nessus start
“ command we can start the nessus.
- After we have to login nessus using a browser.
· https//:127.0.0.1.8834 to
access the nessus home page.
- · So we have to login nessus
Uname : root
Pw : toor
- · Go to scan template and click sacan. They provide this kind of interface.
· In the target box we have to
type victim’s ip address and scan it.
- · After scanning we can get full reports about vulnerabilities. It’s describe all the types
- Here is the scan result says in the host summery
Critical
- 22%
High - 6%
Medium – 13%
Low
- 2%
Others - 63%
- · There are many types of vulnerabilities we can easily exploit critical vulnerabilities.
- · In this case so many critical vulnerabilities.
- · We can choose on and exploit it.
- · I selected 2nd one in this case.
· It’s about the mft IIS 5.0
http printer requeat.
- Now we can exploit the vulnerability against the windows 2000
- · Using metasploit framework we can exploit the vulnerability.
- · To start metasploit and open the terminal, start by installing the data base and the webserver.
- · And also we have to start apache and postgresql server.
- · Using thise commands.
Service apache2 start
Servise postgresql start
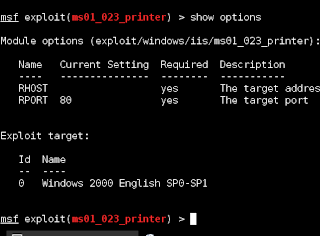
- Use search command to find vulnerability access path.
- · Now you have to type Search ms01.023 this command to find the location of the exploit to take advantage of the MS01.023 CVE 20014-1080 we found earlier.
- Write the user and the RHOST command we can get above image.
- After finally we can exploit the command to our pc to victims pc.
- · After exploiting we can work in victims pc using our commands.
- · We can find the password in the victim’s pc using hushdump command.





















Comments
Post a Comment